Policies & Procedures
Electronic Data Disposal Standards
I. General Statement
The intent of these standards are to minimize the risks of exposing data to unauthorized individuals and inadvertently transferring software to those not licensed to use it. Removing from service and/or repurposing any Electronic Data Storage Device (EDSD) or computer software creates risks for the university. These risks can include unauthorized disclosure of data and the violation of software license agreements, copyrights or other intellectual property that might be stored. Any EDSD, especially those containing restricted data, must have all data sanitized prior to disposal as specified by these standards and the terms of any licensed software.
II. Definition
- Electronic Data Storage Device (EDSD): Any device requiring electrical power to be capable of storing and/or processing data, such as those containing volatile memory and/or magnetic or optical storage. This includes but is not limited to hard drives of personal computers, servers, mainframes, Personal Digital Assistants (PDAs), routers, firewalls, switches, tapes, diskettes, CDs, DVDs, cell phones, smart phones, printers, multifunction devices, digital cameras, flash memory cards or SD cards, and Universal Serial Bus (USB) data storage devices.
III. Matrices Of The Data Disposal Standards
- Cycle Matrix of Data Disposal:
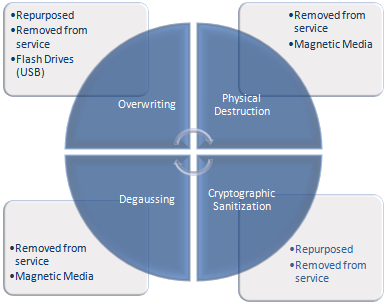
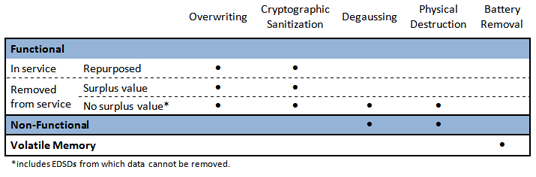
- Standards Matrix of Data Disposal:
IV. Standards
The sanitization of data must be performed on an EDSD in a manner that gives assurance that the data cannot be read and/or recovered.
- All EDSDs shall be sanitized at the earliest time after being taken out of use but not later than 60 days.
- Multi-user EDSDs, such as lab and loaner pool computers, will be sanitized between users as time permits, but not less than annually.
- All documentation and communication must be completed as outlined in section E for any EDSD.
- The method used for data disposal depends upon the functional state of the EDSD.
- A Functional EDSD that will be repurposed or removed from service and has surplus value shall be overwritten or cryptographically sanitized prior to disposal. If the EDSD is to be removed from services and has no surplus value, it shall be overwritten, cryptographically sanitized, physically destroyed or degaussed.
- If the EDSD is non-functional, it shall be physically destroyed or degaussed.
- Data stored in volatile memory, in both functional and non-functional EDSDs, shall be disposed of as outlined in section D.5.
- The following sections outline the acceptable methods of data disposal from any EDSD.
- Overwriting: Overwriting of data means replacing previously stored data with a predetermined pattern of meaningless information. The overwriting process, including the software products and applications used for the overwriting process, shall be capable of:
- Overwriting the entire EDSD, independent of any limitation that the EDSD may have, making it impossible to read and/or recover any intelligible data.
- Overwriting a minimum of one pass of pseudo random data or zeros on all sectors, blocks, tracks and any unused disk space on the entire EDSD.
- Verifying that all data has been sanitized. This verification can be either a separate process or included as part of the software used for overwriting.
- (1) Verification on flash memory, to include USB data storage devices and solid state drives, shall be suspect.
- (2) If data is not completely overwritten, and sanitization fails verification, then overwriting is not an acceptable method of data disposal and another approved method must be applied.
- Degaussing: Degaussing is a process whereby the magnetic media is sanitized. EDSDs seldom can be used after degaussing.
Please note that extreme care should be used when using degaussers since this equipment can cause damage to nearby telephones, monitors, and other EDSDs. Also, the use of a degausser does not guarantee that all data on the EDSD will be sanitized. The following steps shall be followed when EDSDs are degaussed:- Follow the product manufacturer's directions carefully. It is essential to determine the appropriate rate of coercivity for degaussing.
- Shielding materials (cabinets, mounting brackets), which may interfere with the degaussing equipment magnetic field, shall be removed from the EDSD before degaussing.
- Hard disk platters shall be degaussed during the degaussing process in accordance with the manufacturer's specifications.
- Physical Destruction: Physical destruction shall be accomplished to an extent that precludes any possible restoration of the data. The following steps shall be followed when EDSDs are destroyed:
- Cut the electrical connection to the EDSD.
- Shielding materials (cabinets, mounting brackets), which may cause injury during EDSD destruction, shall be removed from the EDSD before destruction begins.
- The EDSD should then be subjected to physical force or extreme temperatures that will disfigure, bend, mangle or otherwise mutilate the EDSD so it is unreadable. Acceptable means of destruction include:
- (1) pulverization (pounding with a sledge hammer)
- (2) incineration and melting
- (3) shredding and disintegration
- (4) Multiple holes drilled into the hard disk platters
- Destruction by end users is not recommended. CD-ROM discs do not require extensive destruction. Discs that are outdated or no longer needed may be rendered unreadable by cutting in half or deep scratching the data side (the shiny side without the label) with a nail, screwdriver, or similar tool. Two deep radial scratches extending from the small inner hole to the outer edge are sufficient to prevent unauthorized access to the data. These discs may be placed in the general waste stream for disposal.
- Cryptographic Sanitization: Sanitization by cryptography works by first encrypting all data as it is written to the EDSD. The only way to read or recover data protected in this manner is to use a valid decryption key. Instant and thorough sanitization occurs when the decryption key is destroyed.
See the university Encryption Policy, as well as the Minimum Encryption Standards. - Data Disposal from Volatile Memory Media: Any EDSD that holds data or configurations in volatile memory shall have all data sanitized by either the removal of the battery or electricity supporting the volatile memory or by such other method recommended by the manufacturer for an EDSD where the battery is not removable. This often includes computer equipment that has memory such as personal computers, PDAs, routers, firewalls and switches.
- Overwriting: Overwriting of data means replacing previously stored data with a predetermined pattern of meaningless information. The overwriting process, including the software products and applications used for the overwriting process, shall be capable of:
- Documentation and Communication: Any disposal action, including certifying that the data has been effectively disposed of, shall be completed in accordance with the following:
- The following information regarding the data disposal process shall be documented prior to an EDSD being removed from service and/or repurposed and communicated to the new user/consumer:
- All individually identifiable Number(s), such as Asset Tag Number(s), Serial Number(s), etc. that are uniquely associated with the EDSD from which data is being sanitized.
- The type of EDSD from which data is being sanitized.
- The date of the data disposal.
- The method(s) used for data disposal.
- The name of the person responsible for the data disposal.
- The name and signature of the person's supervisor.
- The completed documentation shall be maintained in a secure location and available for audit.
- The communication to the new user/consumer shall accompany the sanitized EDSD. Communication must include one of the following:
- Certification Tagging:
- (1) Certification Tags may be printed on a label that is size-appropriate to the EDSD. Preferably the tags will be printed in red letters for ease of recognition.
- (2) Certification Tags must be affixed to the EDSD such that:
- For individual EDSDs such as hard drives, or PDAs, and networked appliances, a certification tag shall be affixed to each EDSD.
- For multiples of EDSDs such as CDs, tapes, etc. a certification tag shall be completed for each physically aggregated lot by affixing the certification tag to the storage container or shrink wrapped pallet. Lots must be aggregated when there is more than one person per function per lot (i.e. more than one data disposer, or more than one quality assurance tester, etc.).
- Acknowledgement via "Terms of Use" (Data Disposal Certification in a document signed by the new user/consumer.)
- Certification Tagging:
- The following information regarding the data disposal process shall be documented prior to an EDSD being removed from service and/or repurposed and communicated to the new user/consumer:
Approved by the Chief Information Officer, April 27, 2011.
