Data Security
Below is information that you should be aware of regarding the handling of Longwood's restricted data. This information is also available as a Data Handling and Classification presentation. If you would like someone to come to your group to give the presentation, contact Information Security at infosec@longwood.edu.
What is Data Classification?
Three categories (Public, Internal and Restricted) were developed to aid in the identification of the sensitivity1 of the university's data; hence Data Classification.
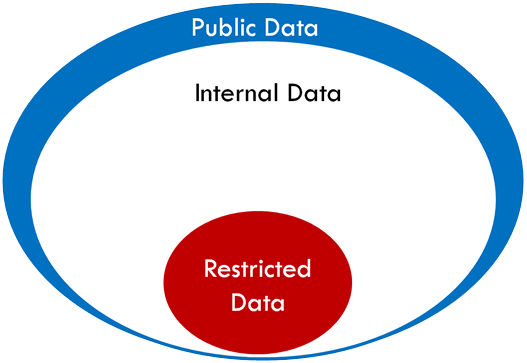
Rings of Data Classification
- Public Data is the least sensitive information and is acceptable for public consumption.
- Internal Data is moderately sensitive information. All university data is considered Internal unless classified otherwise.
- Restricted Data is highly sensitive information for which an unauthorized disclosure may result in identity theft or university liability for costs or damages under laws, government regulations or contract.
Data Classification Links
- Data Classification Policy
- Data Classifications (coming soon)
What is Restricted Data?
Personally Identifiable Information
One example of restricted data is Personally Identifiable Information, or PII, as defined by the Code of Virginia § 18.2-186.6.
|
Personally Identifiable Information (PII) |
|
|
One of these elements |
Combined with one of these elements |
|
|
|
Note: A taxpayer identification number in combination with the income tax withheld for that taxpayer is also PII. |
Personal Health Information
Another example of restricted data is Personal Health Information, or PHI, as defined by the Code of Virginia § 32.1-127.1:05.
|
Personal Health Information (PHI) |
|
|
One of these elements |
Combined with one of these elements |
|
|
Other Regulations, Laws and Standards
Other regulations, laws and standards that enumerate restricted data include:
- HIPAA: The Health Insurance Portability and Accountability Act
- GLBA: The Gramm-Leach-Bliley Act
- PCI DSS: Payment Card Industry Data Security Standards
What is Data Handling?
Standards were developed to set minimum requirements for the protection of data that is stored, transmitted or disposed of; hence the Data Handling Standards.
These standards include recurring requirements, such as approval, encryption, and redaction.
| What is Encryption? | What is Redaction? |
 |
 |
- Encryption: the transformation of data through the use of an algorithmic process into a form in which there is a low probability of assigning meaning without the use of a confidential process or key
- Redaction: the alteration or truncation of data such that no more than the following are accessible as part of the personal information:
- Five digits of a social security number; or
- The last four digits of a driver's license number, state identification card number, or account number.
Data Handling Links
What can I do now?
- Contact User Support Services and inquire about having Spirion installed on your computer.
- If a Spirion scan determines that there is restricted data on your computer, follow the flow chart below immediately:

Note: The "Shred" option in Spirion allows for the secure removal of data. Data "Shredded" with Spirion is totally and permanently removed from your computer.
- If you still have questions email the Information Security Office at infosec@longwood.edu
Why bother?
Good question, because you don't have to if...
- You can work with the data from the Data Owners pre-approved share.
- You can take another hassle-free route:
- For instance, if you only need the last 4 of a social, then delete the rest of it.
- Erase the File: Use the Eraser software to completely and totally remove the file from your non-network space
- Redact the data from the file: Use the delete key to remove what you don't need.
But, if you've decided to keep the data in its restricted form...
Here are some potential consequences of unauthorized disclosure of that data:
- OUCH :: BUDGET
A potential fine; levied by the Commonwealth, up to $150,000 per breach. - OUCH :: REPUTATION
A potential blow on state and local media (i.e. radio, television, etc.); as the university's trustworthiness comes into question. - OUCH :: CUSTOMER SATISFACTION
A potential increase in phone calls, emails and general customer relations; as the university community wonders "Was my data breached?"
1Sensitivity is the degree of adverse effect a compromise of confidentiality, integrity or availability would have on Commonwealth of Virginia interests, the conduct of university programs or the privacy to which individuals are entitled.
